Why Secure Excel Sheets? A Stepbystep Guide

Excel sheets are an invaluable tool for businesses and individuals alike, allowing for efficient data storage, analysis, and management. However, with the increasing sophistication of cyber threats and the potential for unauthorized access, ensuring the security of Excel sheets has become a critical concern. This comprehensive guide will delve into the importance of securing Excel sheets and provide a step-by-step process to implement robust security measures.
Understanding the Risks: A Necessity for Secure Excel Sheets

The first step in securing Excel sheets is understanding the potential risks and vulnerabilities associated with them. Excel files can contain sensitive information, ranging from financial data to personal details, making them an attractive target for cybercriminals. Without proper security measures, these files can be susceptible to various threats, including:
- Unauthorized Access: Unprotected Excel sheets can be accessed by unauthorized individuals, either through physical access to the device or via network vulnerabilities. This can lead to data breaches and the exposure of sensitive information.
- Data Tampering: Malicious actors may modify or delete critical data within Excel sheets, leading to inaccurate analysis, disrupted business operations, or even financial loss.
- Malware Infiltration: Excel files can be a gateway for malware, allowing attackers to introduce malicious code into an organization's network. This can result in data theft, system disruptions, or the spread of viruses.
- Phishing and Social Engineering: Cybercriminals often use Excel files as a vehicle for phishing attacks, where they manipulate users into providing sensitive information or downloading malicious software.
By recognizing these risks, organizations and individuals can take proactive measures to secure their Excel sheets and protect their data. This guide will outline a comprehensive strategy to mitigate these threats and ensure data integrity and confidentiality.
Step 1: Password Protection - The First Line of Defense
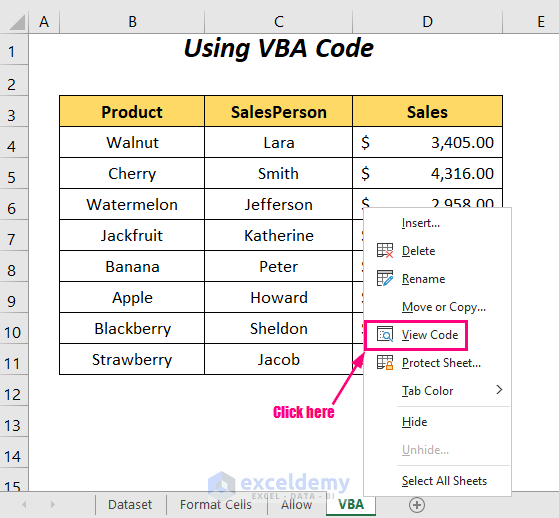
Password protection is a fundamental security measure for Excel sheets. It serves as the initial barrier against unauthorized access, ensuring that only authorized individuals can open and modify the data. Here’s a detailed guide on implementing effective password protection:
Setting Up Password Protection
- Open the Excel sheet you wish to protect.
- Go to the Review tab and select Protect Sheet or Protect Workbook, depending on your needs.
- A dialog box will appear, allowing you to set a password and specify the actions that users will be allowed to perform, such as adding or deleting rows and columns.
- Choose a strong password that combines uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable passwords like dates or common words.
- Confirm the password and click OK. Excel will prompt you to save the file to apply the password protection.
Best Practices for Password Protection
- Use Complex Passwords: Ensure that your passwords are difficult to guess and unique for each Excel sheet. Consider using a password manager to generate and store complex passwords securely.
- Avoid Sharing Passwords: Sharing passwords via email or other insecure channels can compromise security. Instead, use secure methods like encrypted messaging or password-protected documents to share passwords with authorized individuals.
- Regularly Update Passwords: Change passwords periodically to minimize the risk of unauthorized access. Set a schedule for password updates and ensure that all authorized users are informed of the changes.
Step 2: Encryption - Fortifying Data Security

Encryption is a powerful tool for securing Excel sheets, as it transforms the data into an unreadable format, accessible only to those with the correct decryption key. This step adds an extra layer of security, ensuring that even if an unauthorized individual gains access to the file, they cannot decipher the contents without the proper encryption key.
Implementing Encryption
- Open the Excel sheet and go to the File tab.
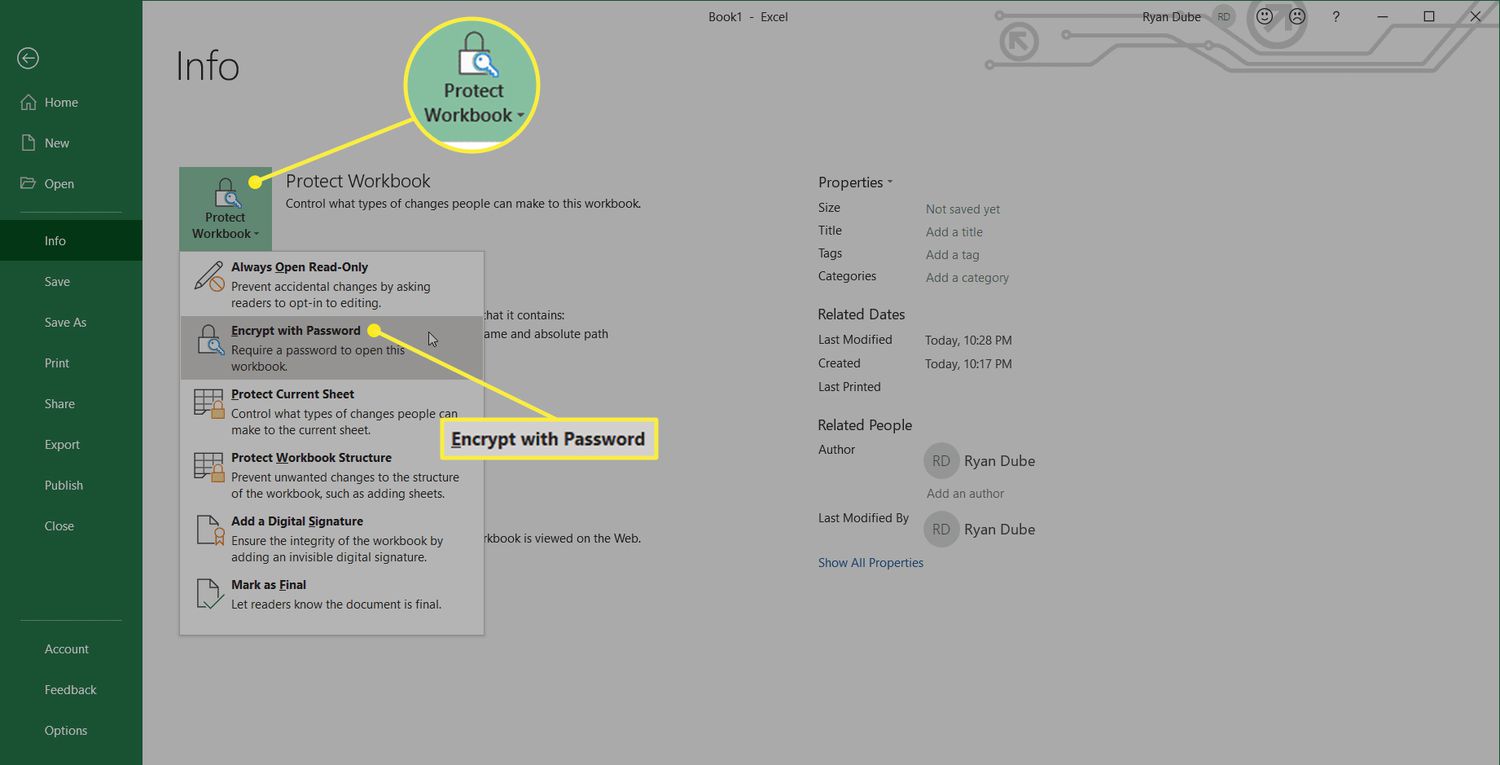
- Select Info and then click on Protect Workbook.
- Choose Encrypt with Password and enter a strong password. Confirm the password and click OK.
- Save the file, and Excel will apply the encryption. From now on, the file will require the encryption key to be opened.
Encryption Best Practices
- Use Strong Encryption Algorithms: Ensure that your Excel version supports robust encryption algorithms like AES-256. These algorithms provide a higher level of security and make it virtually impossible for attackers to decrypt the data.
- Secure Key Management: Properly store and manage encryption keys. Consider using a key management system to ensure the keys are securely backed up and accessible only to authorized personnel.
- Regularly Update Encryption Protocols: Stay updated with the latest encryption standards and protocols. As technology advances, older encryption methods may become less secure. Regularly review and update your encryption practices to maintain the highest level of protection.
Step 3: Access Control - Restricting User Permissions
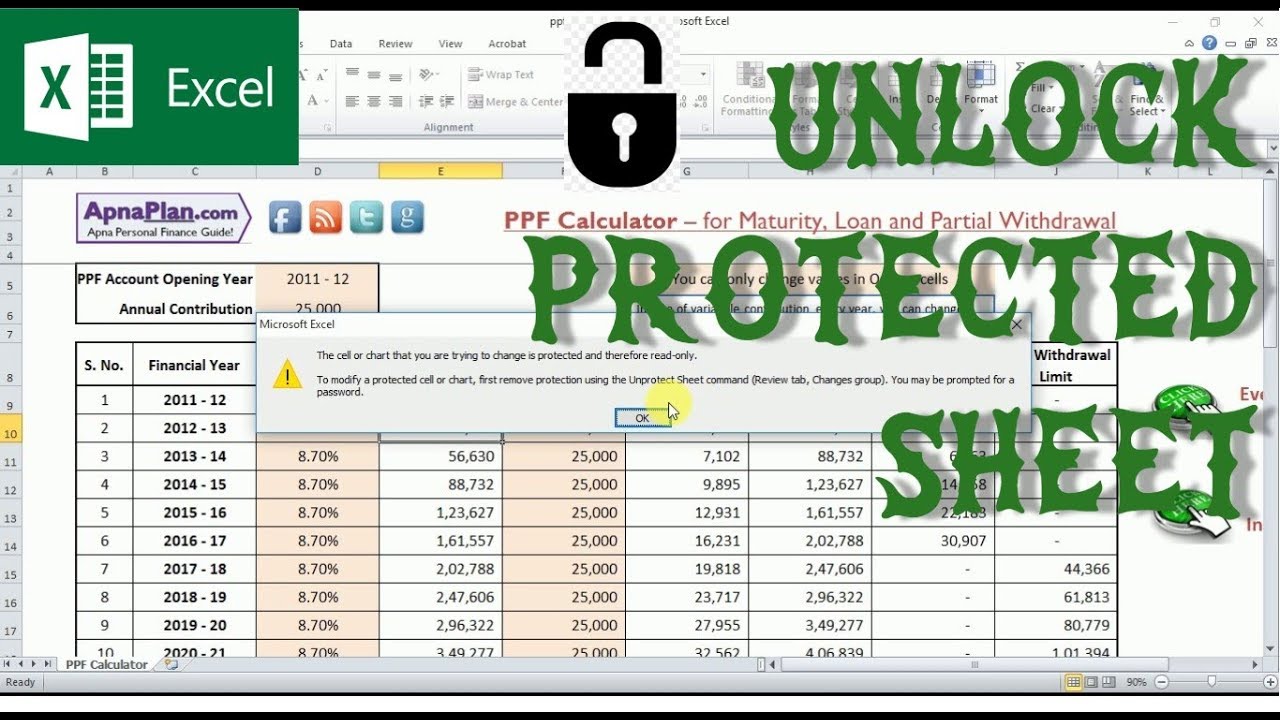
Access control is crucial for securing Excel sheets, as it allows administrators to define and restrict user permissions. By carefully managing who can access, modify, or distribute the data, organizations can minimize the risk of unauthorized data manipulation or exposure.
Implementing Access Control
- Open the Excel sheet and go to the Review tab.
- Click on Protect Sheet and set a password (if not already done). This will restrict access to the sheet.
- To further control user permissions, go to the Review tab and select Share Workbook.
- In the Allow Changes section, specify the users who are authorized to make changes to the sheet. You can also set specific actions that users are allowed to perform, such as inserting or deleting rows.
- Save the file, and the access control settings will be applied.
Access Control Best Practices
- Role-Based Access Control (RBAC): Implement RBAC to assign specific permissions to user roles within the organization. This ensures that only individuals with the necessary privileges can access and modify sensitive data.
- Regularly Review and Update Permissions: Periodically review and update user permissions to reflect organizational changes and security best practices. Revoke access for individuals who no longer require it, and ensure that permissions are granted on a need-to-know basis.
- Audit Logging: Enable audit logging to track and monitor user activities within Excel sheets. This helps detect any unauthorized access attempts or suspicious activities, allowing for prompt response and mitigation of potential security breaches.
Step 4: Data Validation - Ensuring Data Integrity

Data validation is an essential step in securing Excel sheets, as it helps ensure the accuracy and integrity of the data. By implementing data validation rules, organizations can prevent unauthorized or erroneous data entry, reducing the risk of data corruption or manipulation.
Implementing Data Validation
- Select the cell or range of cells for which you want to apply data validation.
- Go to the Data tab and click on Data Validation.
- In the Data Validation dialog box, select the Settings tab.
- Choose the validation criteria, such as whole numbers, decimals, or text length. You can also specify a custom formula to define the validation rules.
- Set error alerts to provide feedback to users when invalid data is entered. This helps guide users to enter accurate data.
- Click OK to apply the data validation rules.
Data Validation Best Practices
- Use Clear and Concise Validation Rules: Ensure that your validation rules are easy to understand and follow. Clear rules reduce the likelihood of user errors and improve data integrity.
- Provide User-Friendly Error Messages: When invalid data is entered, provide helpful and informative error messages. This guides users to correct their input and reduces frustration.
- Regularly Review and Update Validation Rules: As your Excel sheets evolve and data requirements change, review and update your validation rules to ensure they remain relevant and effective.
Step 5: Backup and Recovery - Mitigating Data Loss Risks

Implementing a robust backup and recovery strategy is crucial for securing Excel sheets. It ensures that even if data loss occurs due to accidental deletion, system failure, or cyberattacks, organizations can quickly restore their data and minimize downtime.
Setting Up Backup and Recovery
- Identify the critical Excel sheets that require regular backups.
- Determine the backup frequency based on the importance and frequency of updates to the sheets.
- Use Excel’s built-in backup feature or third-party backup software to create regular backups of your Excel sheets.
- Store backups in a secure, off-site location, such as a cloud storage service or an external hard drive.
- Test the backup and recovery process periodically to ensure that you can successfully restore your Excel sheets in the event of data loss.
Backup and Recovery Best Practices
- Regular Backups: Establish a consistent backup schedule to ensure that your Excel sheets are regularly backed up. The frequency of backups should align with the rate of changes and the criticality of the data.
- Secure Backup Storage: Store backups in a secure location that is protected from unauthorized access and potential cyber threats. Consider using encryption for added security.
- Test and Verify Backups: Regularly test your backup and recovery process to ensure its effectiveness. Verify that you can successfully restore your Excel sheets from the backups, and address any issues promptly.
Step 6: User Education and Awareness - A Critical Security Measure

While technical security measures are essential, user education and awareness play a crucial role in securing Excel sheets. Employees and users must be trained to recognize potential security threats and follow best practices to minimize the risk of data breaches.
Implementing User Education
- Develop a comprehensive security awareness training program that covers Excel sheet security best practices.
- Educate users about the importance of password protection, encryption, and access control, and provide guidance on creating strong passwords and securely managing encryption keys.
- Train users to recognize and report potential security threats, such as phishing attempts or suspicious activities.
- Encourage a culture of security awareness by promoting regular security discussions and providing resources for users to stay informed about the latest threats and best practices.
User Education Best Practices
- Regular Training Sessions: Conduct periodic security awareness training sessions to keep users informed about the latest security threats and best practices. Refreshers can help reinforce security habits and address any emerging concerns.
- Tailored Training: Customize your training materials to address the specific security needs and challenges of your organization. Consider the different roles and responsibilities of your employees and provide targeted guidance accordingly.
- Incentivize Security Awareness: Recognize and reward employees who demonstrate a strong commitment to security practices. This can encourage others to follow suit and foster a culture of security awareness throughout the organization.
Step 7: Regular Security Audits - Ensuring Ongoing Protection
Regular security audits are essential to maintain the security of Excel sheets and identify potential vulnerabilities. By conducting thorough audits, organizations can proactively address security weaknesses and ensure that their security measures remain effective over time.
Conducting Security Audits
- Identify the critical Excel sheets that require regular security audits.
- Establish a schedule for conducting security audits, considering the sensitivity and frequency of changes to the sheets.
- Use Excel’s built-in auditing tools or third-party security auditing software to analyze the sheets for potential vulnerabilities.
- Review the audit results and address any identified issues promptly. This may involve updating security measures, implementing additional controls, or providing further user training.
Security Audit Best Practices
- Comprehensive Auditing: Conduct thorough security audits that cover all aspects of Excel sheet security, including password protection, encryption, access control, and data validation. Leave no stone unturned to ensure comprehensive protection.
- Continuous Monitoring: Implement continuous monitoring systems to detect and respond to potential security incidents in real-time. This allows for prompt action and minimizes the impact of any security breaches.
- Collaborative Auditing: Engage a team of security experts or collaborate with external security professionals to conduct security audits. A diverse perspective can help identify vulnerabilities that might otherwise be overlooked.
Conclusion: A Secure Future for Excel Sheets

Securing Excel sheets is a multifaceted process that requires a combination of technical measures, user education, and ongoing vigilance. By following the steps outlined in this guide, organizations and individuals can significantly enhance the security of their Excel sheets, protecting sensitive data from unauthorized access and potential threats.
As cyber threats continue to evolve, it is essential to stay updated with the latest security practices and technologies. Regularly review and update your security measures to ensure they remain effective against emerging threats. By adopting a proactive and comprehensive approach to Excel sheet security, you can safeguard your data and maintain the integrity of your operations.
What are some common challenges in securing Excel sheets, and how can they be overcome?
+One of the main challenges is striking a balance between security and usability. Implementing strong security measures can sometimes hinder the ease of access and collaboration. To overcome this, organizations should:
- Establish a clear security policy that defines the appropriate use of Excel sheets and outlines the security measures to be followed.
- Provide users with training and resources to understand the importance of security and how to navigate the security measures effectively.
- Regularly review and update security measures to ensure they remain user-friendly and do not create unnecessary barriers to productivity.
How can organizations ensure that their Excel sheet security measures are effective and up-to-date?
+Regular security audits and vulnerability assessments are crucial to identify potential gaps in security measures. Organizations should:
- Conduct periodic security audits to review the effectiveness of their security measures and identify any weaknesses or vulnerabilities.
- Stay informed about the latest security threats and best practices by subscribing to security newsletters, attending industry conferences, and engaging with security professionals.
- Continuously update and enhance their security measures based on the findings of security audits and emerging threats.
What are some alternative methods for securing Excel sheets, especially for organizations with specific security requirements?
+In addition to the measures outlined in this guide, organizations with specific security requirements may consider the following alternatives:
- Implementing a Virtual Private Network (VPN) to encrypt all data transmitted over the network, including Excel sheets.
- Using cloud-based Excel sheet storage and collaboration platforms that offer advanced security features, such as multi-factor authentication and granular access controls.
- Integrating Excel sheets with a secure document management system that provides robust security features, such as digital signatures and version control.



