Ssh On Mac
Secure Shell (SSH) is a powerful cryptographic network protocol that enables secure communication between devices over an unsecured network. It is widely used for remote access, command execution, and data transfer, providing a secure and encrypted connection for sensitive operations. This guide will delve into SSH's functionality, configuration, and usage on macOS, empowering users to securely connect to remote servers and manage their systems efficiently.
Understanding SSH on macOS

SSH is an integral part of macOS, offering a secure and efficient way to manage remote servers and devices. The macOS Terminal application provides a command-line interface for interacting with SSH, allowing users to establish connections, execute commands, and transfer files securely.
Key Concepts and Components
SSH operates on a client-server model, where the client initiates the connection to the server. The server authenticates the client using various methods, including password-based authentication, public-key authentication, and certificate-based authentication. Once authenticated, the client can access the server’s resources securely.
- SSH Client: The SSH client is the software used to initiate connections to remote servers. On macOS, the default SSH client is OpenSSH, which is pre-installed and accessible via the Terminal application.
- SSH Server: The SSH server is the software running on the remote machine that accepts and manages incoming connections. Common SSH server implementations include OpenSSH and Dropbear SSH.
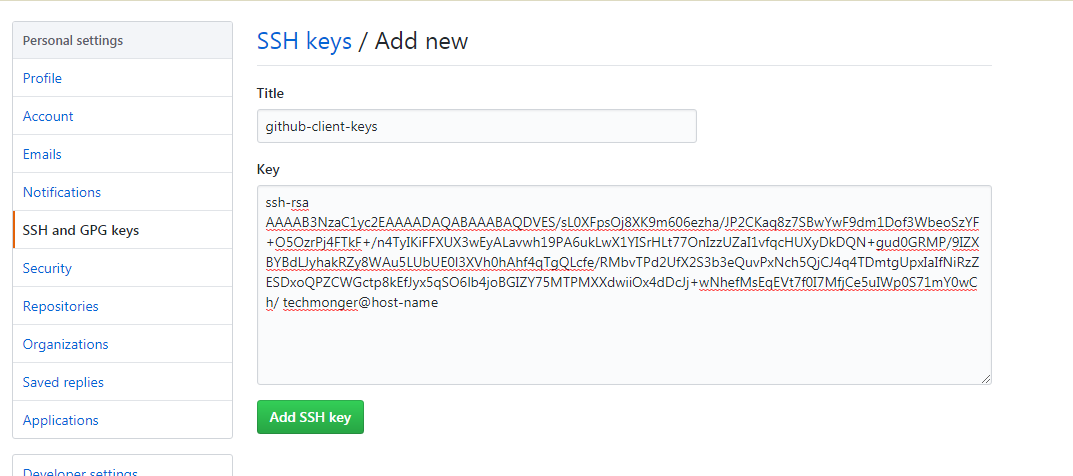
- SSH Keys: SSH keys are cryptographic keys used for authentication. They consist of a private key, which is kept secure on the client machine, and a public key, which is shared with the server. When a client connects to a server, the server uses the public key to verify the client's identity.
- SSH Config File: The SSH config file, located at ~/.ssh/config, allows users to configure and manage SSH connections. It contains settings such as host names, user names, port numbers, and authentication methods, providing a convenient way to manage multiple SSH connections.
Getting Started with SSH on macOS
To begin using SSH on macOS, follow these steps:
Installing OpenSSH (if not already installed)
OpenSSH is typically pre-installed on macOS. However, if it is not present, you can install it using the Homebrew package manager:
brew install openssh
Generating SSH Keys
SSH keys are essential for secure authentication. To generate SSH keys on macOS, follow these steps:
- Open the Terminal application.
- Enter the following command to generate a new SSH key pair:
This command generates an RSA key with a length of 4096 bits and associates it with your email address.ssh-keygen -t rsa -b 4096 -C "your_email@example.com" - When prompted, choose a secure location to store the key and enter a strong passphrase. The passphrase adds an extra layer of security to your private key.
- Accept the default file name and location for the key, or specify a custom path if desired.
Adding SSH Keys to the SSH Agent
To use SSH keys for authentication, you need to add them to the SSH agent. The SSH agent is a program that stores your private keys in memory, allowing you to connect to remote servers without entering your passphrase each time.
- Open the Terminal application.
- Start the SSH agent by entering the following command:
eval "$(ssh-agent -s)" - Add your private key to the SSH agent:
Replace id_rsa with the name of your private key file if it is different.ssh-add ~/.ssh/id_rsa
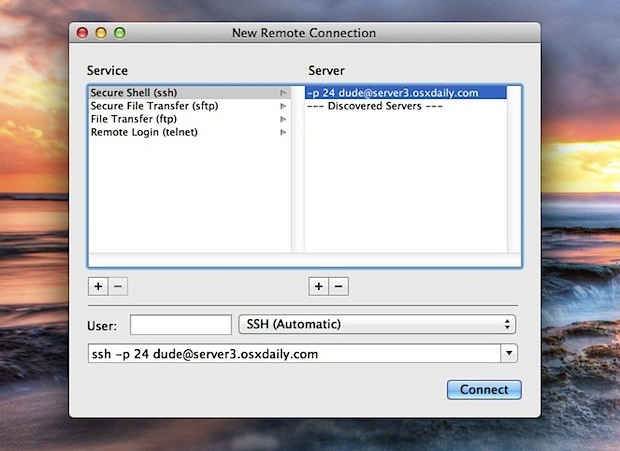
Connecting to a Remote Server with SSH

Once you have generated SSH keys and added them to the SSH agent, you can connect to a remote server securely using SSH. Follow these steps:
- Open the Terminal application.
- Enter the following command to connect to the remote server:
Replace username with your username on the remote server and remote_server_ip with the IP address or hostname of the server.ssh username@remote_server_ip - If it is the first time connecting to the server, you will be prompted to confirm the server's fingerprint. Type yes and press Enter to continue.
- If you have set a passphrase for your private key, you will be prompted to enter it. The connection will be established once the passphrase is accepted.
Using SSH for Remote Command Execution
SSH allows you to execute commands on a remote server without establishing an interactive session. This is useful for automating tasks and running scripts remotely.
ssh username@remote_server_ip "command_to_execute"
Transferring Files with SSH
SSH supports secure file transfer using the Secure Copy (SCP) protocol. SCP allows you to copy files between local and remote systems securely.
Uploading Files to a Remote Server
scp local_file_path username@remote_server_ip:remote_file_path
Downloading Files from a Remote Server
scp username@remote_server_ip:remote_file_path local_file_path
Advanced SSH Configuration and Usage

SSH offers a wide range of configuration options and advanced features to enhance security and usability. Here are some key aspects to explore:
SSH Config File
The SSH config file, ~/.ssh/config, allows you to configure and manage SSH connections. You can define host-specific settings, such as usernames, port numbers, and authentication methods, making it easier to connect to multiple servers.
Port Forwarding
SSH supports port forwarding, which allows you to securely tunnel network traffic through an SSH connection. This is useful for accessing services running on a remote server or for adding an extra layer of security to local services.
Agent Forwarding
Agent forwarding enables you to use your local SSH agent on a remote server. This allows you to authenticate with SSH keys on the remote server without having to manually add the keys to the remote agent.
Dynamic Port Forwarding
Dynamic port forwarding, also known as SOCKS proxy, allows you to create a secure tunnel for network traffic through an SSH connection. This is particularly useful for accessing resources on the remote network that are not directly accessible from your local network.
Customizing SSH Behavior
SSH provides various command-line options and configuration settings to customize its behavior. You can control aspects such as verbosity, connection timeout, and the number of parallel connections.
Security Best Practices

To ensure the security of your SSH connections, consider the following best practices:
- Use SSH keys instead of passwords for authentication. SSH keys provide stronger security and eliminate the need to remember complex passwords.
- Regularly update your SSH client and server software to ensure you have the latest security patches and improvements.
- Enable two-factor authentication (2FA) for an extra layer of security. This adds an additional step to the authentication process, making it harder for unauthorized users to access your servers.
- Limit the permissions of your SSH keys to restrict access to specific servers or services. This helps prevent unauthorized access in case your private key is compromised.
- Monitor your SSH logs regularly to detect any suspicious activities or unauthorized access attempts.
Conclusion

SSH is a powerful and versatile tool for securely managing remote servers and devices. By understanding its functionality, configuration, and best practices, you can leverage SSH to streamline your remote administration tasks and ensure secure communication over unsecured networks. With its robust encryption and authentication mechanisms, SSH provides a reliable and trusted solution for remote access and data transfer.
What is the purpose of SSH keys in SSH authentication?
+SSH keys are a pair of cryptographic keys used for authentication. The private key is kept secure on the client machine, while the public key is shared with the server. When a client connects to a server, the server uses the public key to verify the client’s identity, ensuring secure and authenticated connections.
How can I generate SSH keys on macOS?
+To generate SSH keys on macOS, open the Terminal application and enter the following command: ssh-keygen -t rsa -b 4096 -C “your_email@example.com”. This command generates an RSA key with a length of 4096 bits and associates it with your email address. Follow the prompts to choose a secure location and enter a strong passphrase for your private key.
What is the role of the SSH agent in SSH authentication?
+The SSH agent is a program that stores your private SSH keys in memory. By adding your private key to the SSH agent, you can connect to remote servers without entering your passphrase each time. This enhances convenience and security by avoiding the need to repeatedly enter your passphrase.
How can I configure SSH connections using the SSH config file?
+The SSH config file, located at ~/.ssh/config, allows you to configure and manage SSH connections. You can define host-specific settings, such as usernames, port numbers, and authentication methods. This simplifies the process of connecting to multiple servers by providing pre-configured connection details.
What is port forwarding in SSH, and how can it be useful?
+Port forwarding in SSH allows you to securely tunnel network traffic through an SSH connection. This is useful for accessing services running on a remote server or for adding an extra layer of security to local services. By forwarding specific ports, you can create a secure tunnel for data transfer, ensuring confidentiality and integrity.



