Execution Policy Bypass

Execution Policy Bypass is a critical aspect of security and control in the realm of PowerShell, a powerful task automation and configuration management framework. This feature allows administrators to bypass the default execution policies set on a system, providing a flexible and adaptable approach to managing scripts and code execution. With the ability to override these policies, users can execute potentially risky scripts for troubleshooting, testing, or administrative purposes. However, this flexibility also comes with a heightened risk of security breaches and malicious activity, making it crucial to understand and manage this feature effectively.
Understanding Execution Policies
PowerShell execution policies are a fundamental component of its security model. These policies dictate the level of trust that can be placed in scripts and configuration files, helping to prevent the execution of potentially harmful code. By default, PowerShell has a set of execution policies that define the actions that can be taken when a script is encountered. These policies are crucial in preventing unauthorized or malicious code from running on a system.
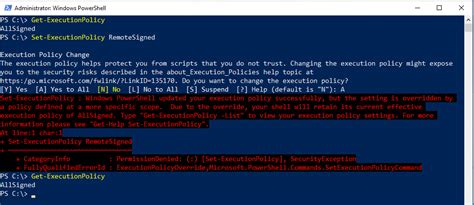
The default execution policy is usually set to Restricted, which means that only signed scripts can be executed. This policy provides a high level of security, ensuring that only trusted scripts can run. However, this can also be a hindrance for administrators and developers who need to execute scripts for testing or troubleshooting purposes. This is where the Execution Policy Bypass comes into play.
Default Execution Policies
PowerShell offers several default execution policies, each with its own level of security and flexibility:
- Restricted: This is the most secure policy, allowing only signed scripts to run. All other scripts, including locally stored ones, are blocked.
- AllSigned: In this policy, all scripts, whether local or remote, must be signed by a trusted publisher. This provides a higher level of security than the Restricted policy, as it ensures that even locally stored scripts are trusted.
- RemoteSigned: RemoteSigned allows the execution of local, unsigned scripts but requires remote scripts to be signed. This policy strikes a balance between security and flexibility, allowing local testing while maintaining some level of security for remote scripts.
- Unrestricted: As the name suggests, this policy allows the execution of all scripts, regardless of their origin or signing status. While it offers the highest level of flexibility, it also carries the highest risk of security breaches.
- Bypass: The Bypass policy is unique in that it does not enforce any execution policy. It allows scripts to run without any checks, providing the highest level of flexibility but also the highest potential for security risks.
These execution policies can be set and modified using the Set-ExecutionPolicy cmdlet. However, changing the execution policy, especially to a more permissive one, should be done with caution, as it can significantly impact the security of the system.
The Need for Execution Policy Bypass
The Execution Policy Bypass feature is particularly useful in scenarios where administrators need to execute scripts that would normally be blocked by the default execution policy. This could be for various reasons, such as:
- Troubleshooting: When an issue arises, administrators often need to execute scripts to diagnose and resolve the problem. These scripts might not be signed or might originate from an untrusted source, thus requiring a bypass of the execution policy.
- Development and Testing: Developers frequently create and test scripts locally before deploying them. The Execution Policy Bypass allows them to test these scripts without the hindrance of strict execution policies.
- Administrative Tasks: Certain administrative tasks might require the execution of scripts that are not signed or are not part of the trusted publisher list. In such cases, the Bypass policy can be a useful tool.
While the Bypass policy provides flexibility, it is essential to use it judiciously. Misuse or abuse of this feature can lead to serious security vulnerabilities, allowing malicious scripts to run unchecked.
Security Implications
The Execution Policy Bypass, when not managed properly, can pose significant security risks. Malicious actors can exploit this feature to execute harmful scripts, potentially leading to data breaches, system compromise, or other malicious activities. Therefore, it is crucial to implement strict access controls and monitoring mechanisms when using this feature.
Administrators should also consider implementing least privilege principles, ensuring that users have the minimum access rights necessary to perform their tasks. This helps to limit the potential damage that can be caused by a security breach.
Implementing Execution Policy Bypass Safely

To ensure that the Execution Policy Bypass is used safely and securely, administrators should follow a set of best practices. These practices include:
- Limited User Access: Restrict the use of the Bypass policy to a small group of trusted administrators. This minimizes the risk of unauthorized access and misuse.
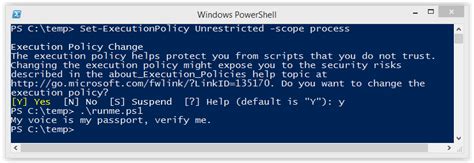
- Temporary Bypass: Instead of setting the execution policy to Bypass permanently, consider using the
-ExecutionPolicy Bypassparameter temporarily when executing specific scripts. This ensures that the Bypass policy is only active when needed. - Script Signing: Encourage developers and administrators to sign their scripts using a trusted certificate. This provides an additional layer of security, ensuring that only signed scripts can run, even when the Bypass policy is in effect.
- Monitoring and Auditing: Implement robust monitoring and auditing mechanisms to track script execution. This allows administrators to quickly identify and respond to any suspicious activity.
- User Education: Educate users about the risks associated with the Execution Policy Bypass. Ensure that they understand the potential security implications and are vigilant in reporting any suspicious activity.
By following these practices, organizations can leverage the flexibility of the Execution Policy Bypass while maintaining a strong security posture.
Best Practices for Secure Script Execution
In addition to the above practices, there are several other measures that can be taken to enhance the security of script execution:
- Code Review: Implement a rigorous code review process for all scripts, especially those that will be executed with elevated privileges. This helps to identify and mitigate potential security risks before the script is deployed.
- Least Privilege Principle: As mentioned earlier, adhering to the principle of least privilege ensures that users have only the necessary permissions to perform their tasks. This limits the potential damage that can be caused by a compromised account.
- Regular Updates: Keep PowerShell and all related software up to date. This ensures that any known security vulnerabilities are patched, reducing the risk of exploitation.
- Network Segmentation: Consider segmenting the network to isolate critical systems and data. This can help to contain the impact of a security breach, preventing it from spreading throughout the entire network.
By combining these best practices with a robust security posture, organizations can effectively leverage the power of PowerShell while maintaining a high level of security.
Real-World Examples and Case Studies

The Execution Policy Bypass feature has been a subject of interest and concern in the cybersecurity community. Several real-world examples and case studies highlight the importance of managing this feature effectively.
Case Study: Malicious Script Execution
In a recent incident, a malicious actor gained access to an organization’s network through a phishing attack. The attacker then used the Execution Policy Bypass feature to execute a series of unsigned, malicious scripts. These scripts allowed the attacker to gain further access to the network, steal sensitive data, and compromise critical systems. The organization suffered significant financial and reputational damage as a result.
This case study underscores the importance of implementing strict access controls and monitoring mechanisms when using the Execution Policy Bypass. It also highlights the need for user education, as the initial phishing attack could have been prevented with proper training and awareness.
Example: Legitimate Script Execution
In a contrasting example, a system administrator used the Execution Policy Bypass to execute a script that was crucial for troubleshooting a critical system issue. The script, which was not signed and originated from an untrusted source, helped the administrator identify and resolve the problem quickly. This case demonstrates the flexibility and utility of the Bypass policy when used responsibly and securely.
However, even in this legitimate use case, the administrator followed strict security protocols. The script was executed in a controlled environment, and its execution was monitored closely. This approach ensured that the script did not cause any unintended damage or security breaches.
Future Implications and Recommendations
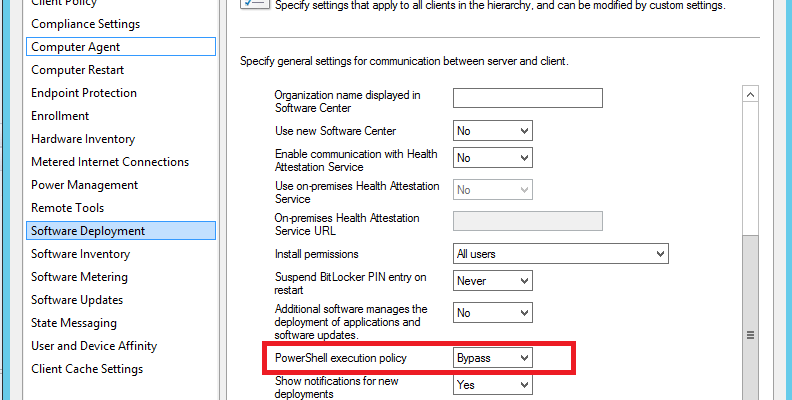
As PowerShell continues to evolve and gain popularity, the Execution Policy Bypass feature will remain a critical aspect of its security model. To ensure the safe and effective use of this feature, administrators and organizations should consider the following recommendations:
- Enhanced User Education: Invest in comprehensive user education programs that cover not only the basics of PowerShell but also the potential security risks and best practices for script execution.
- Improved Monitoring and Detection: Develop advanced monitoring and detection systems that can identify and respond to suspicious script execution in real-time. This can help to mitigate the impact of security breaches.
- Regular Security Audits: Conduct regular security audits to identify potential vulnerabilities and misconfigurations related to the Execution Policy Bypass. This proactive approach can help to prevent security incidents before they occur.
- Collaboration with Security Researchers: Engage with the cybersecurity community and security researchers to stay informed about the latest threats and vulnerabilities related to PowerShell. This collaboration can lead to the development of more robust security measures.
By implementing these recommendations, organizations can leverage the power of PowerShell while maintaining a strong security posture. The Execution Policy Bypass, when used responsibly and securely, can be a valuable tool for administrators and developers, providing the flexibility needed for effective system management without compromising security.
How can I set the Execution Policy Bypass temporarily?
+To set the Execution Policy Bypass temporarily, you can use the -ExecutionPolicy Bypass parameter when executing a script. For example, powershell -ExecutionPolicy Bypass -File script.ps1. This will allow the script to run without any execution policy checks, but the policy will revert to its original setting after the script execution.
What are the risks associated with the Execution Policy Bypass?
+The Execution Policy Bypass carries a high risk of security breaches. When this policy is in effect, any script, regardless of its origin or signing status, can be executed. This can allow malicious actors to run harmful scripts, potentially leading to data breaches, system compromise, or other malicious activities.
How can I sign my scripts for enhanced security?
+To sign your scripts, you’ll need a code signing certificate. You can obtain this certificate from a trusted certificate authority (CA). Once you have the certificate, you can use the Set-AuthenticodeSignature cmdlet to sign your script. This provides an additional layer of security, ensuring that only signed scripts can run, even when the Execution Policy Bypass is in effect.