10 Mac Address Table Secrets To Optimize Your Network Performance

The Media Access Control (MAC) address table, often referred to as the Content Addressable Memory (CAM) table, is a critical component in modern networking infrastructure. This table plays a pivotal role in the efficient operation of network switches, routers, and other network devices. By understanding and optimizing the MAC address table, network administrators can significantly enhance overall network performance, improve scalability, and reduce latency. In this comprehensive guide, we will delve into ten secrets that will empower you to optimize your network performance by leveraging the full potential of the MAC address table.
1. Understanding the MAC Address Table Structure

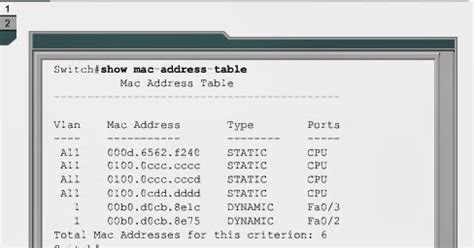
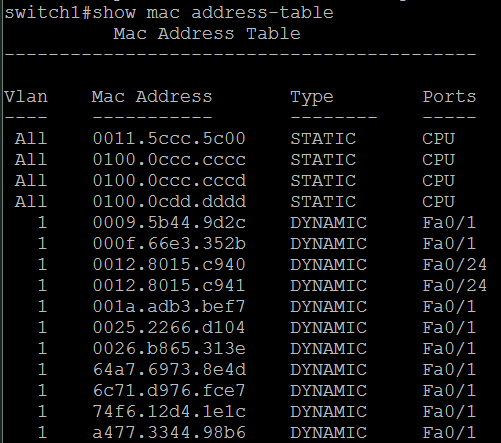
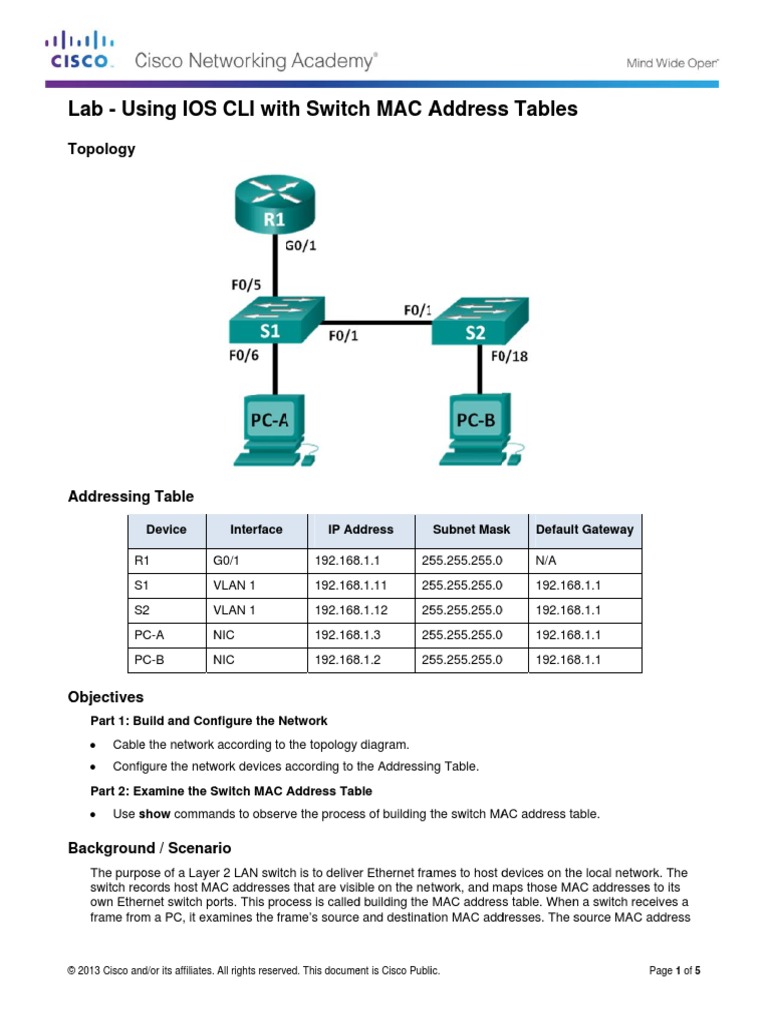
The MAC address table is a fundamental data structure within network devices that maps MAC addresses to specific network ports. This table is responsible for forwarding data packets to their intended destinations based on the destination MAC address. Understanding the structure and dynamics of this table is crucial for effective network management.
Table Structure and Organization
The MAC address table is typically organized as a lookup table, with each entry containing a MAC address and the corresponding port number. The table is indexed by the MAC address, allowing for rapid lookup and forwarding decisions. The size and capacity of the table vary depending on the network device’s hardware and software capabilities.
| MAC Address | Port Number |
|---|---|
| 00:1A:2B:3C:4D:5E | 1 |
| AA:BB:CC:DD:EE:FF | 2 |
| ... | ... |

Dynamic Nature of the MAC Address Table
The MAC address table is dynamic, meaning it is continuously updated as devices connect and disconnect from the network. Network devices employ various protocols, such as the Address Resolution Protocol (ARP) and the Spanning Tree Protocol (STP), to maintain an accurate and up-to-date table. These protocols help in resolving MAC addresses, detecting network loops, and ensuring efficient data forwarding.
2. Optimizing MAC Address Table Size and Capacity

The size and capacity of the MAC address table directly impact the performance and scalability of your network. A well-optimized table ensures efficient forwarding of data packets, minimizes collisions, and reduces latency. Here’s how you can optimize the MAC address table size and capacity:
Sizing the MAC Address Table
Network devices have a finite capacity for storing MAC addresses in their tables. It’s essential to size the table appropriately based on the expected number of connected devices. Oversized tables can lead to unnecessary memory consumption, while undersized tables may result in frequent table updates and potential performance degradation.
To determine the optimal size, consider the following factors:
- Number of connected devices: Estimate the maximum number of devices that will be connected to the network simultaneously.
- Device mobility: If devices frequently move between ports, a larger table size may be required to accommodate dynamic changes.
- Network topology: Take into account the network's topology and the number of switches or routers involved.
Increasing Table Capacity
If you anticipate a high number of connected devices or a dynamic network environment, it's crucial to increase the MAC address table capacity. This can be achieved through the following methods:
- Upgrading hardware: Invest in network devices with larger memory capacities and advanced MAC address table management features.
- Implementing CAM table expansion: Some network devices support CAM table expansion, allowing you to add additional memory modules to increase table size.
- Segmenting the network: Divide the network into smaller segments with dedicated switches or routers, reducing the burden on individual devices.
3. Implementing Efficient MAC Address Learning
Efficient MAC address learning is crucial for maintaining an accurate and up-to-date MAC address table. Network devices employ various techniques to learn and update MAC addresses, ensuring that data packets are forwarded to the correct destinations.
Address Resolution Protocol (ARP)
ARP is a critical protocol for resolving IP addresses to MAC addresses. When a device needs to send a packet to a specific IP address, it broadcasts an ARP request to discover the corresponding MAC address. The device with the matching IP address responds with its MAC address, which is then learned and added to the MAC address table.
Port Security and Dynamic Address Learning
Port security features can be utilized to control and manage MAC address learning on individual ports. By enabling port security, you can limit the number of allowed MAC addresses per port, preventing unauthorized devices from joining the network. Dynamic address learning ensures that only legitimate devices can learn and update MAC addresses on a port.
MAC Address Table Aging and Flushing
MAC address table aging is a process where unused or outdated entries are automatically removed from the table after a certain period. This helps in keeping the table up-to-date and prevents unnecessary memory consumption. Additionally, you can manually flush specific MAC addresses or the entire table to force a refresh.
4. Preventing MAC Address Table Overflows
MAC address table overflows can occur when the table becomes full, leading to performance degradation and potential network outages. It’s crucial to implement measures to prevent such overflows and ensure the stability of your network.
Monitoring Table Utilization
Regularly monitor the utilization of the MAC address table to identify any signs of congestion or potential overflows. Network management tools and protocols, such as Simple Network Management Protocol (SNMP), can provide real-time data on table utilization and help you stay proactive.
Implementing Rate Limiting and Filtering
Rate limiting and filtering can be applied to control the rate at which MAC addresses are learned and added to the table. By setting appropriate thresholds, you can prevent rapid and excessive MAC address learning, especially in environments with high device mobility.
MAC Address Filtering and Whitelisting
Implementing MAC address filtering and whitelisting can help restrict unauthorized devices from joining the network. By configuring a whitelist of approved MAC addresses, you can ensure that only known and trusted devices are allowed to learn and update MAC addresses in the table.
5. Utilizing Advanced MAC Address Table Features
Modern network devices offer a range of advanced features and capabilities to enhance MAC address table management and optimize network performance. Leveraging these features can provide significant benefits in terms of efficiency, scalability, and security.
Static MAC Address Assignment
Static MAC address assignment allows you to manually configure and assign MAC addresses to specific ports. This is particularly useful in environments where devices have fixed IP addresses and MAC addresses, such as servers or critical network infrastructure components. By statically assigning MAC addresses, you can ensure consistent and predictable forwarding decisions.
MAC Address Spoofing Detection and Prevention
MAC address spoofing is a security threat where an attacker attempts to impersonate a legitimate device by using a different MAC address. Advanced network devices offer features to detect and prevent such attacks. These features include MAC address authentication, verification, and monitoring, ensuring that only authorized devices can access the network.
Dynamic Host Configuration Protocol (DHCP) Snooping
DHCP snooping is a security feature that helps prevent DHCP-based attacks and improves MAC address table accuracy. By enabling DHCP snooping, the network device inspects and validates DHCP messages, ensuring that only legitimate DHCP servers are providing IP addresses to clients. This prevents unauthorized devices from obtaining IP addresses and potentially causing MAC address table inconsistencies.
6. Optimizing MAC Address Table Lookup and Forwarding
Efficient MAC address table lookup and forwarding are critical for minimizing latency and maximizing network throughput. By optimizing these processes, you can ensure that data packets are forwarded quickly and accurately to their intended destinations.
Hardware-Assisted MAC Address Lookup
Network devices with advanced hardware capabilities can offload MAC address lookup and forwarding tasks to specialized hardware components. This hardware acceleration significantly reduces the processing overhead on the main CPU, resulting in faster lookup times and improved overall network performance.
Content-Addressable Memory (CAM) Architecture
CAM is a specialized type of memory used in network devices to store and search MAC address tables. CAM provides extremely fast lookup times, typically in a single clock cycle, making it an ideal choice for high-performance networks. By leveraging CAM architecture, network devices can achieve near-instantaneous MAC address lookups and efficient forwarding decisions.
MAC Address Aggregation and Compression
In large-scale networks with a high density of connected devices, MAC address aggregation and compression techniques can be employed to optimize table size and lookup efficiency. These techniques involve grouping similar or adjacent MAC addresses into a single entry, reducing the overall table size while maintaining accurate forwarding decisions.
7. Enhancing MAC Address Table Security
Securing the MAC address table is crucial to prevent unauthorized access, data breaches, and network disruptions. By implementing robust security measures, you can protect your network infrastructure and ensure the integrity of your MAC address table.
MAC Address Authentication and Verification
Implementing MAC address authentication and verification mechanisms adds an extra layer of security to your network. These mechanisms involve validating the authenticity of MAC addresses before allowing them to learn and update the table. This helps prevent unauthorized devices from joining the network and reduces the risk of MAC address spoofing attacks.
Access Control Lists (ACLs) and MAC Address Filtering
ACLs and MAC address filtering allow you to control and restrict network access based on MAC addresses. By creating ACLs that specify allowed and denied MAC addresses, you can ensure that only authorized devices can communicate on the network. This provides an additional layer of security, especially in environments with sensitive data or critical infrastructure.
Secure Shell (SSH) and Remote Access
Secure remote access to network devices is essential for managing and configuring MAC address tables. SSH provides a secure and encrypted connection for remote management, ensuring that unauthorized users cannot gain access to sensitive network settings and configurations.
8. Monitoring and Troubleshooting MAC Address Table Issues

Effective monitoring and troubleshooting of MAC address table issues are crucial for maintaining network stability and performance. By identifying and resolving problems promptly, you can prevent network outages and ensure a seamless user experience.
Network Monitoring and Diagnostics
Utilize network monitoring tools and protocols, such as SNMP and Syslog, to collect real-time data and logs related to MAC address table operations. These tools provide insights into table utilization, errors, and potential bottlenecks, helping you identify and resolve issues promptly.
Error Handling and Logging
Implement robust error handling and logging mechanisms to capture and record any errors or exceptions related to MAC address table operations. This allows you to track and analyze issues, identify patterns, and take proactive measures to prevent future occurrences.
Network Troubleshooting and Debugging
Develop a comprehensive network troubleshooting and debugging process to address MAC address table-related issues. This process should include steps for identifying and isolating problems, gathering relevant data, and implementing appropriate solutions. Regularly review and refine this process based on real-world experiences to ensure its effectiveness.
9. Integrating MAC Address Table Management with Network Automation
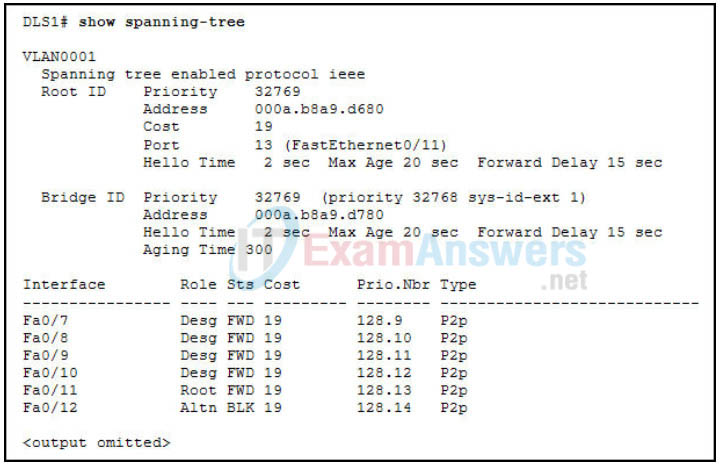
Network automation plays a vital role in modern network management, and integrating MAC address table management with automation tools can significantly enhance efficiency and scalability. By automating routine tasks and processes, you can free up valuable time and resources for more strategic initiatives.
Network Configuration Management
Implement network configuration management tools that can automatically synchronize and backup MAC address table configurations across multiple devices. This ensures consistency and simplifies the process of managing and updating MAC address tables in large-scale networks.
Policy-Based Management and Automation
Leverage policy-based management and automation frameworks to define and enforce MAC address table policies across your network infrastructure. These policies can include rules for MAC address learning, aging, and filtering, ensuring consistent and automated management of the table.
Programmable Network Devices and APIs
Modern network devices often expose APIs and programming interfaces that allow for automated configuration and management. By utilizing these APIs, you can integrate MAC address table management into your network automation workflows, enabling efficient and dynamic updates based on real-time network conditions.
10. Future Trends and Innovations in MAC Address Table Management

The field of MAC address table management is continuously evolving, with new technologies and innovations shaping the future of network performance optimization. Staying abreast of these trends and innovations can help you stay ahead of the curve and leverage the latest advancements to optimize your network.
Software-Defined Networking (SDN)
SDN is a transformative technology that separates the control plane from the data plane, allowing for centralized management and control of network devices. In the context of MAC address table management, SDN enables dynamic and flexible configuration, policy enforcement, and real-time adjustments based on network traffic patterns.
Intelligent MAC Address Learning and Forwarding
Advanced network devices are incorporating machine learning and artificial intelligence algorithms to optimize MAC address learning and forwarding decisions. These algorithms can analyze network traffic patterns, predict future MAC address needs, and dynamically adjust table configurations to optimize performance.
Network Function Virtualization (NFV)
NFV involves virtualizing network functions, such as MAC address table management, onto commodity hardware. This virtualization approach provides flexibility, scalability, and cost-effectiveness, allowing you to dynamically allocate resources based on network demands.
How often should I monitor the MAC address table utilization?
+Monitoring the MAC address table utilization on a regular basis is crucial for proactive network management. It is recommended to establish a monitoring schedule that aligns with the network's peak usage periods and critical operations. This ensures that any potential issues or anomalies can be identified and addressed promptly.
<div class="faq-item">
<div class="faq-question">
<h3>What are the signs of a MAC address table overflow?</h3>
<span class="faq-toggle">+</span>
</div>
<div class="faq-answer">
<p>Signs of a MAC address table overflow may include increased packet loss, slow network performance, and frequent network outages. Additionally, you may observe devices becoming unreachable or experiencing connectivity issues. Monitoring tools and network diagnostics can help identify these symptoms and provide insights into the underlying causes.</p>
</div>
</div>
<div class="faq-item">
<div class="faq-question">
<h3>How can I implement MAC address filtering effectively?</h3>
<span class="faq-toggle">+</span>
</div>
<div class="faq-answer">
<p>To implement MAC address filtering effectively, start by identifying the critical network segments and devices that require protection. Create a whitelist of approved MAC addresses for these segments and configure the network devices to allow only those addresses. Regularly review and update the whitelist to ensure it remains up-to-date and accurate.</p>
</div>
</div>
</div>



